The End of Egress Fees: The Year of "Sovereign Cloud"
Say goodbye to egress fees. In 2026, sovereign cloud lets businesses own their data, cut costs, and escape centralized cloud lock-in.
Digitalization in Legal Sector: Compliant, Confidential, and Cloud-Ready
Understanding Legal Digitalization for Law Firms and Legal Departments Legal digitalization is the secure modernization of legal workflows, transforming paper-based processes into digital legal systems that are efficient, compliant, and privacy-focused. This process leverages secure legal technology such as encrypted legal cloud storage, digital case management software, and confidential legal
Key Factors for Ultimate Security and Privacy in Data Storage Solutions
In this blog, we debunk myths about secure data storage, explaining why end-to-end encryption isn’t enough. Your data should be encrypted on your device, with keys staying on your computer, ensuring you alone control and access your data, even if the multiple cloud provider is hacked. What Is Secure
Is Google Password Manager Really Safe? What You Need to Know
When it comes to storing your most sensitive digital credentials, not all password managers are created for the same purpose. While Google Password Manager has common usage, it falls short in areas that matter most: transparency, security, and user control. Let’s break down why you should reconsider using Google’
WeTransact Enhances its Password Security with TransferChain Pass
WeTransact is a SaaS company streamlining the way businesses publish and sell their applications on Microsoft Marketplace. After woking at +7 years at Microsoft and experiencing inefficiencies of managing and selling hundreds of SaaS apps, WeTransact was founded in 2023 by Founders Johan Aussenac, Juan Jose Castiblanques and Dick Dijkstra
What Is SFTP & It's Limitations in Secure Data Transfer
For a long period of time, Secure File Transfer Protocol (SFTP) was considered a go-to solution for securely transferring data. Despite its widespread use, SFTP is showing its age and is increasingly being challenged by modern data transfer needs. In this article, we will be talking about the for main
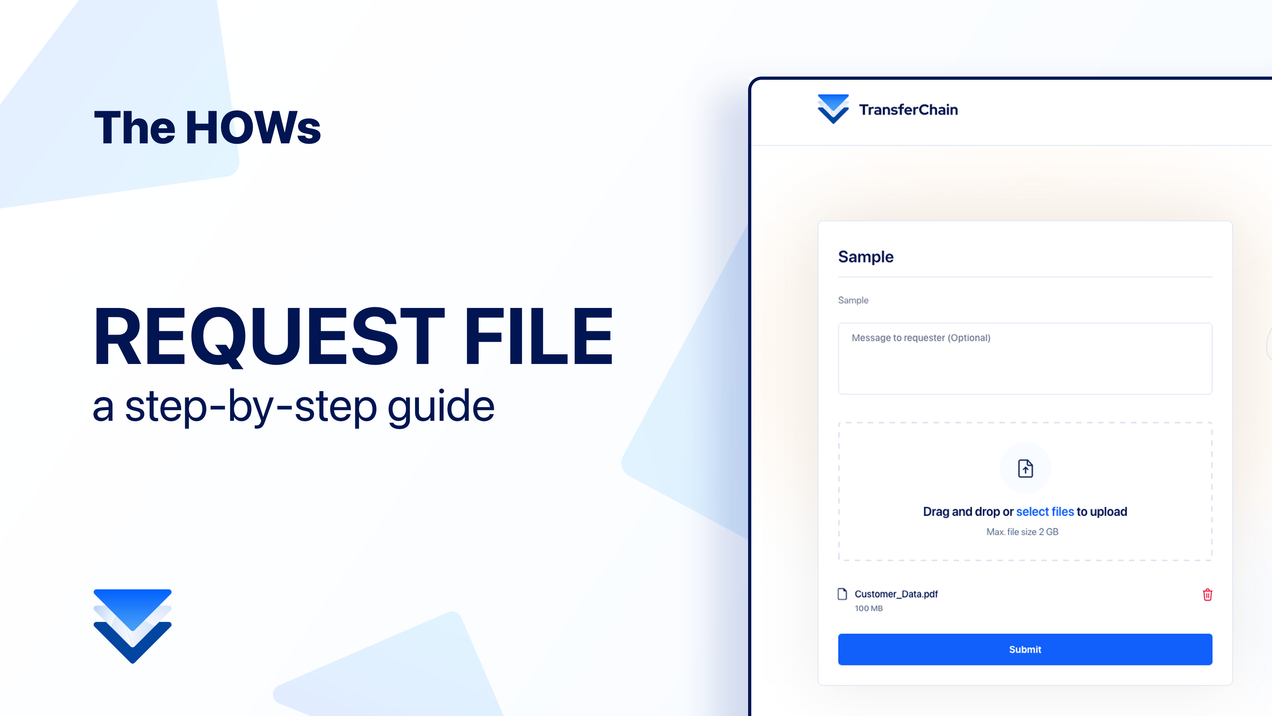
Request files – The HOWs
How do you request files? Here’s a step-by-step guide. 1- To create a new file request, go to “File Requests” in your Drive account 2- Click the "+ New File Request" button. 3- Adjust your settings, then generate a secure link. For enhanced security, consider enabling two-factor authentication
What Is a Business Password Manager and Why Do You Need It?
Nearly everyone online has some kind of a method for managing their passwords, whether it’s using variations of a familiar phrase or saving them in their browser. While these simple approaches might seem to work, they are often not the most secure options. You will most likely find yourself
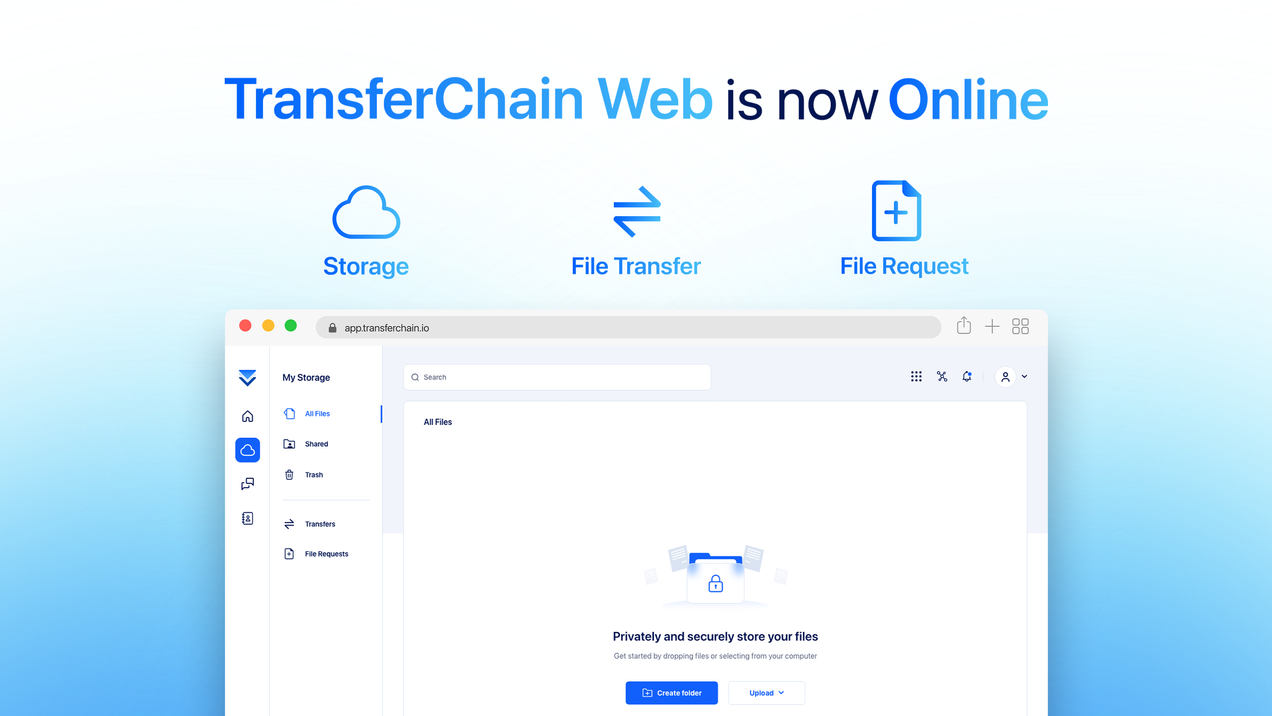
Introducing Blockchain-integrated TransferChain Web Access
Last week, we launched a new feature that many of our users have requested: TransferChain Web We have created the safest way to access your files directly from a browser. On top of that, you can now start using TransferChain without having to install an app. This not only improved
Will ChatGPT Take Our Jobs or Our Privacy?
Let's start by stating what we will say at the end: No, this blog was not written with ChatGPT. And again, no, artificial intelligence will not take away everyone's jobs. Since ChatGPT has become popular, users have been expressing concerns about their professions in this and
Privacy and Security can Coexist
From the moment we are born, security becomes a basic need and is followed by privacy when we start becoming individuals. We want to store our personal information, dialogs, and memories securely and we rely on familiar solutions that we believe to be secure to do so. What we read
Decentralization Ensures Privacy and Security
Centralized Structures Managed by a central authority, these structures operate according to the rules that are set by that authority. Numerous central structures are ingrained in our traditional, everyday lives including databases, health systems, financial systems, and fintech technologies. For instance, central banks in many countries function as central authorities