Discover latest features, stories and thoughts about web3, cloud, privacy and data security.
The Convenience Conspiracy: How Your Habits Fund a $270 Billion Criminal Enterprise
The Human Factor Crisis In the shadowy world of cybercrime, success isn't measured by technical sophistication—it's measured by efficiency. While security professionals focus on building impenetrable digital fortresses, cybercriminals have discovered something far more profitable: exploiting the predictable patterns of human behavior. The uncomfortable truth
Digitalization in Legal Sector: Compliant, Confidential, and Cloud-Ready
Understanding Legal Digitalization for Law Firms and Legal Departments Legal digitalization is the secure modernization of legal workflows, transforming paper-based processes into digital legal systems that are efficient, compliant, and privacy-focused. This process leverages secure legal technology such as encrypted legal cloud storage, digital case management software, and confidential legal
Key Factors for Ultimate Security and Privacy in Data Storage Solutions
In this blog, we debunk myths about secure data storage, explaining why end-to-end encryption isn’t enough. Your data should be encrypted on your device, with keys staying on your computer, ensuring you alone control and access your data, even if the multiple cloud provider is hacked. What Is Secure
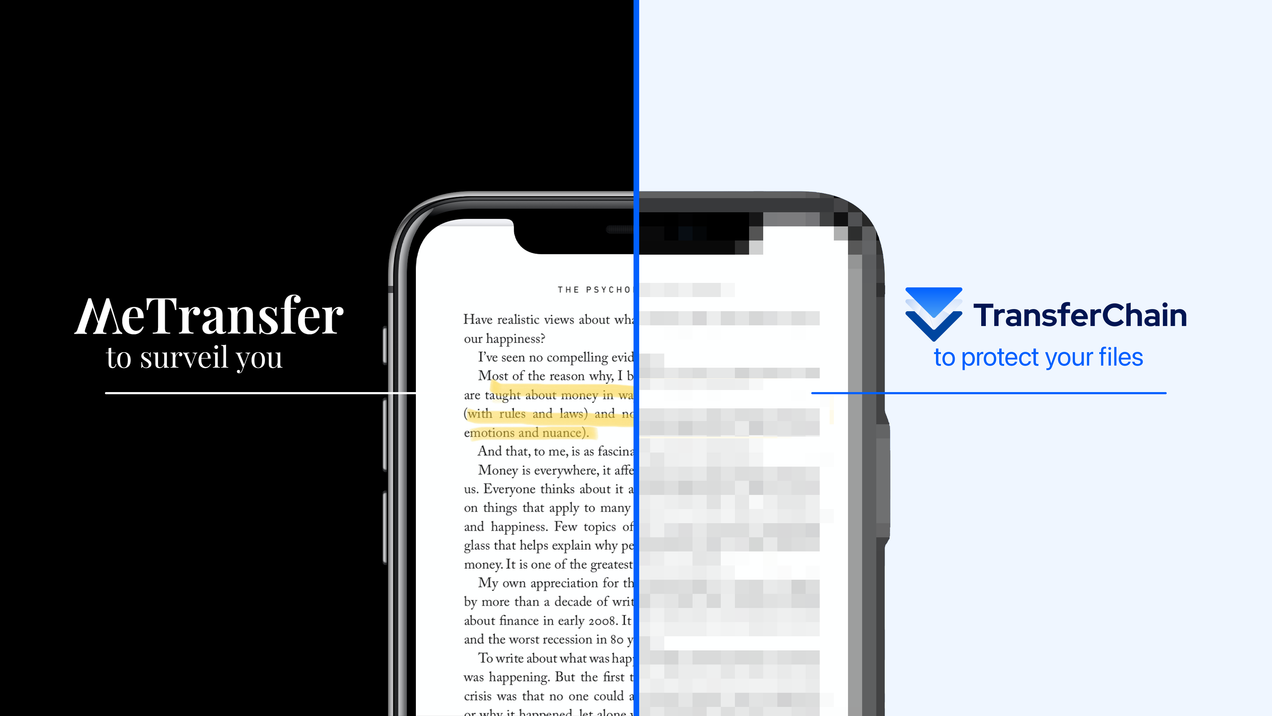
Why WeTransfer’s Latest Terms Are a Privacy Breach in Disguise
Did You Just Sign Away Your Work? For years, WeTransfer has promised a frictionless way to share large files. But buried in their [terms of service](https://wetransfer.com/explore/legal/terms)—effective August 8th—is a seismic shift that redefines what happens to your data the second you hit
New at TransferChain - Q2 2025
We're continuing to push boundaries in Q2 with updates that bring more flexibility and a smoother experience across TransferChain.
Is Google Password Manager Really Safe? What You Need to Know
When it comes to storing your most sensitive digital credentials, not all password managers are created for the same purpose. While Google Password Manager has common usage, it falls short in areas that matter most: transparency, security, and user control. Let’s break down why you should reconsider using Google’
The Inseparable Trinity: Data Security, Privacy, and User Confidentiality
Where data flows freely and technology permeates every aspect of our lives, the concepts of data security, privacy, and user confidentiality have become increasingly intertwined and crucial. While often used interchangeably, these represent distinct yet interconnected pillars of information protection. As we navigate through 2025, a fundamental truth is becoming
The Scaling Challenge: Why On-Premise Storage Struggles in the Age of Data Explosion
Struggling with data growth? Discover why cloud & decentralized storage are overtaking outdated on-premise systems.
Client-Side Encryption vs. Server-Side Encryption: What’s the Difference?
Every day, we use products and services that store our sensitive data, making data protection more critical than ever. With cyber threats constantly evolving, robust encryption is essential. Two popular encryption methods—client-side encryption (CSE) and server-side encryption (SSE)—offer distinct approaches to securing your information. This blog breaks down
Scalability Solutions in Blockchain: Navigating Layer 1 and Layer 2 Approaches
The Blockchain Scalability Challenge Blockchain technology has promised to revolutionize various industries with its decentralized, secure, and transparent nature. However, as adoption grows, the limitations of current blockchain systems become increasingly apparent. At the heart of this challenge lies the blockchain trilemma: the difficulty in achieving optimal levels of security,
New at TransferChain - Q1 2025
We’re stepping into 2025 with a fresh wave of updates focused on smarter control, smoother interactions, and even stronger protection. Here’s what’s new this quarter!
WeTransact Enhances its Password Security with TransferChain Pass
WeTransact is a SaaS company streamlining the way businesses publish and sell their applications on Microsoft Marketplace. After woking at +7 years at Microsoft and experiencing inefficiencies of managing and selling hundreds of SaaS apps, WeTransact was founded in 2023 by Founders Johan Aussenac, Juan Jose Castiblanques and Dick Dijkstra