
What Is SFTP & It's Limitations in Secure Data Transfer
For a long period of time, Secure File Transfer Protocol (SFTP) was considered a go-to solution for securely transferring data. Despite its widespread use, SFTP is showing its age and is increasingly being challenged by modern data transfer needs.
In this article, we will be talking about the for main challenges of SFTP, exploring advanced alternatives, and providing critical insights for Chief Information Security Officers.
What Is Secure File Transfer Protocol (SFTP)?
SFTP (SSH File Transfer Protocol) is a network protocol that enables secure file transfer and management by leveraging the encryption and authentication mechanisms of Secure Shell (SSH). Technically, it encrypts both commands and data on a single connection (typically over port 22), supports robust authentication methods (such as password-based logins and SSH key pairs), and offers file system operations like resuming interrupted transfers, directory listings, and remote file deletion
However, SFTP faces four main challenges:
- lack of automation,
- integration difficulties,
- security gaps, and
- poor scalability.
Consequently, it’s becoming a legacy solution unable to meet modern data transfer needs.
In the following section, we are going to dive in these challenges, and how TransferChain addresses each one of them.
Four Main Challenges of SFTP in Modern Data Transfer
Challenge 1: Absence of Native Automation Features in SFTP
SFTP was originally designed purely for secure file transfers and does not include built‐in automation features such as scheduling, error handling, logging, or notifications. As a result, any automation must be implemented through external scripting (using shell scripts, cron jobs, or third‐party tools), which increases the complexity and risk of human error.
For example, system administrators often have to create custom “here‐document” scripts to connect, transfer files, and then manually manage error conditions and log results. This patchwork solution can be brittle as operations scale, requiring continuous maintenance and troubleshooting—challenges that managed file transfer (MFT) solutions address with integrated, low-code automation features.
Solution 1. How Could We Help in Automating Fast and Secure Data Transfer?
As TransferChain, we extend the automation capabilities of SFTP by integrating advanced file-sharing and security functionalities.
Traditional SFTP often requires additional layers for encryption; in contrast, TransferChain incorporates built-in client-side encryption to secure data throughout the transfer process.
Its data fragmentation feature automatically splits large files into smaller, encrypted segments, improving transfer speeds while preserving security—capabilities that SFTP does not inherently provide.
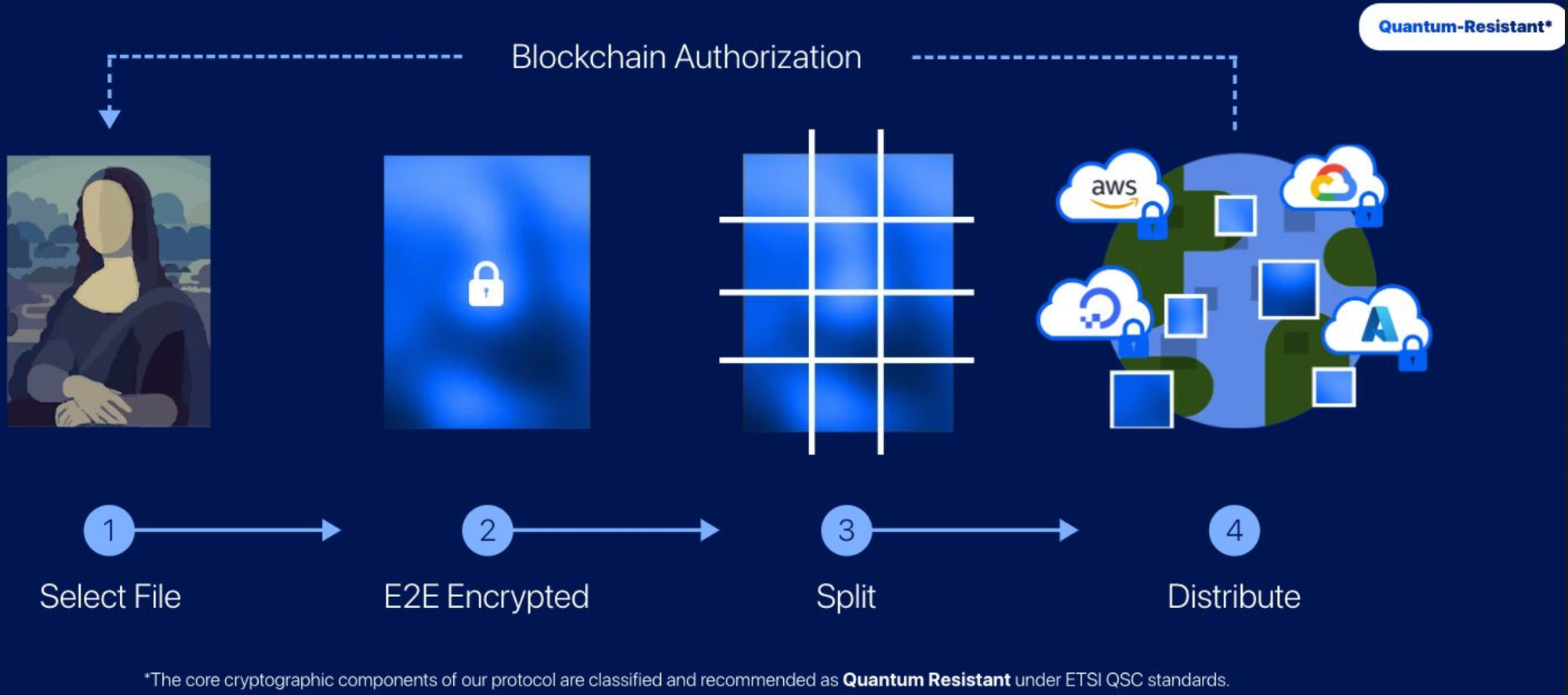
Additionally, TransferChain employs blockchain-based authorization to ensure file transfers are auditable and tamper-proof, offering a level of traceability and integrity not available in standard SFTP. TransferChain also provides APIs for integration with existing systems, enabling automated workflows and reducing the need for manual intervention typical of traditional SFTP processes.
Finally, it offers greater flexibility in adapting to various cloud environments, supporting scalable automation strategies across different cloud providers without compromising security.
Challenge 2: Integration Challenges of SFTP
The main problem is that SFTP doesn’t natively support API-driven integration.
In practice, you have to build a middleware layer to "translate" between the SFTP protocol and the modern APIs used by cloud platforms, CRMs, or ERPs. This extra layer increases complexity, requires additional coding and maintenance, and introduces extra points of failure.
Any changes in the API or the underlying SFTP environment might break the integration, resulting in potential downtime and increased troubleshooting efforts.
Solution 2: How Could TransferChain Integrate?
As stressed in precious solution, TransferChain is engineered at the protocol level, enabling direct API integration and eliminating the need for middleware.
We can look at this from a real-life case that we often see from our customers.
When a customer uploads a file through your custom-designed website interface, TransferChain seamlessly manages the backend file transfer via its integrated API. This design ensures that the entire file transfer process is both efficient and reliable.
Want to see it yourself in action, try it now!
Challenge 3: Security Concerns of Secure File Transfer Protocol (SFTP)
While SFTP ensures that data is encrypted during transit, it does not inherently provide protection for data at rest. This means that files stored on the server remain vulnerable unless additional encryption measures are applied.
Moreover, SFTP was designed primarily for secure file transfer rather than comprehensive system security; as such, it generally lacks advanced features like multi-factor authentication (MFA) and granular access controls that are standard in modern security architectures.
Solution 3: How Can We Help as the Most Secure Solution?
We designed the TransferChain protocol to overcome the inherent limitations of SFTP by embracing a modern, comprehensive approach to data security and privacy—both during transfer and when stored at rest.
Unlike SFTP, which primarily relies on legacy SSH-based encryption methods, TransferChain leverages a sophisticated blend of state-of-the-art cryptographic techniques.
Data is protected in transit using a combination of Elliptic Curve Cryptography (secp256k1) and Ed25519 digital signatures, while AES-256 in GCM and CTR modes, along with the efficient Salsa20 stream cipher, ensures that every piece of information is securely encrypted as it moves across networks.
But the advantages of TransferChain don’t stop at data in motion. Recognizing that safeguarding stored data is equally critical, TransferChain also ensures that all data at rest is encrypted using industry-standard algorithms. Every encryption, hashing, and key exchange process—be it the client-side key management and Diffie-Hellman exchange enhanced with Poly1305, or the secure address generation via ECDSA with SHA-512—has been carefully integrated to provide end-to-end security.
This means that even if unauthorized access were attempted, the data remains unreadable and protected by layers of robust, proven cryptography.
By handling key management on the client side, TransferChain eliminates the vulnerabilities associated with server-side key storage, offering unmatched privacy. Additionally, its design includes forward secrecy and unique address generation for every transaction, ensuring that even if a key is compromised, past communications remain secure.
Overall, TransferChain’s architecture provides a level of integrated, continuous encryption—both in transit and at rest—that far surpasses the traditional, less flexible model of SFTP, making it a superior choice for today’s demanding, data-driven environments.
Challenge 4: Scalability Issues
SFTP struggles to accommodate the on-demand scaling required in cloud or hybrid environments. Its reliance on fixed infrastructure makes it challenging to handle large data volumes or transfers across geographically dispersed locations.
Solution 4: How Could We Help for Advanced Scalability
We address SFTP’s scalability limitations by providing a cloud-native solution with dynamic scaling capabilities.
Unlike SFTP, which often requires manual infrastructure adjustments, TransferChain dynamically adapts to varying workloads, making it well-suited for cloud and hybrid environments with fluctuating demand.
Our distributed network efficiently manages large data volumes across multiple cloud providers, enabling seamless on-demand scaling.
By employing data splitting techniques, we process large files in parallel across different cloud environments, improving throughput without overloading the system. TransferChain integrates blockchain-based authorization to maintain security during scaling, preventing vulnerabilities that traditional systems often face.
By leveraging multiple cloud providers, we optimize resource allocation, reduce costs, and prevent bottlenecks caused by underutilized infrastructure.
This combination of scalability, flexibility, and security helps address SFTP’s shortcomings, making TransferChain a more adaptable solution for modern cloud and hybrid infrastructures.
Introducing TransferChain: The Future of Secure and Decentralized File Transfers
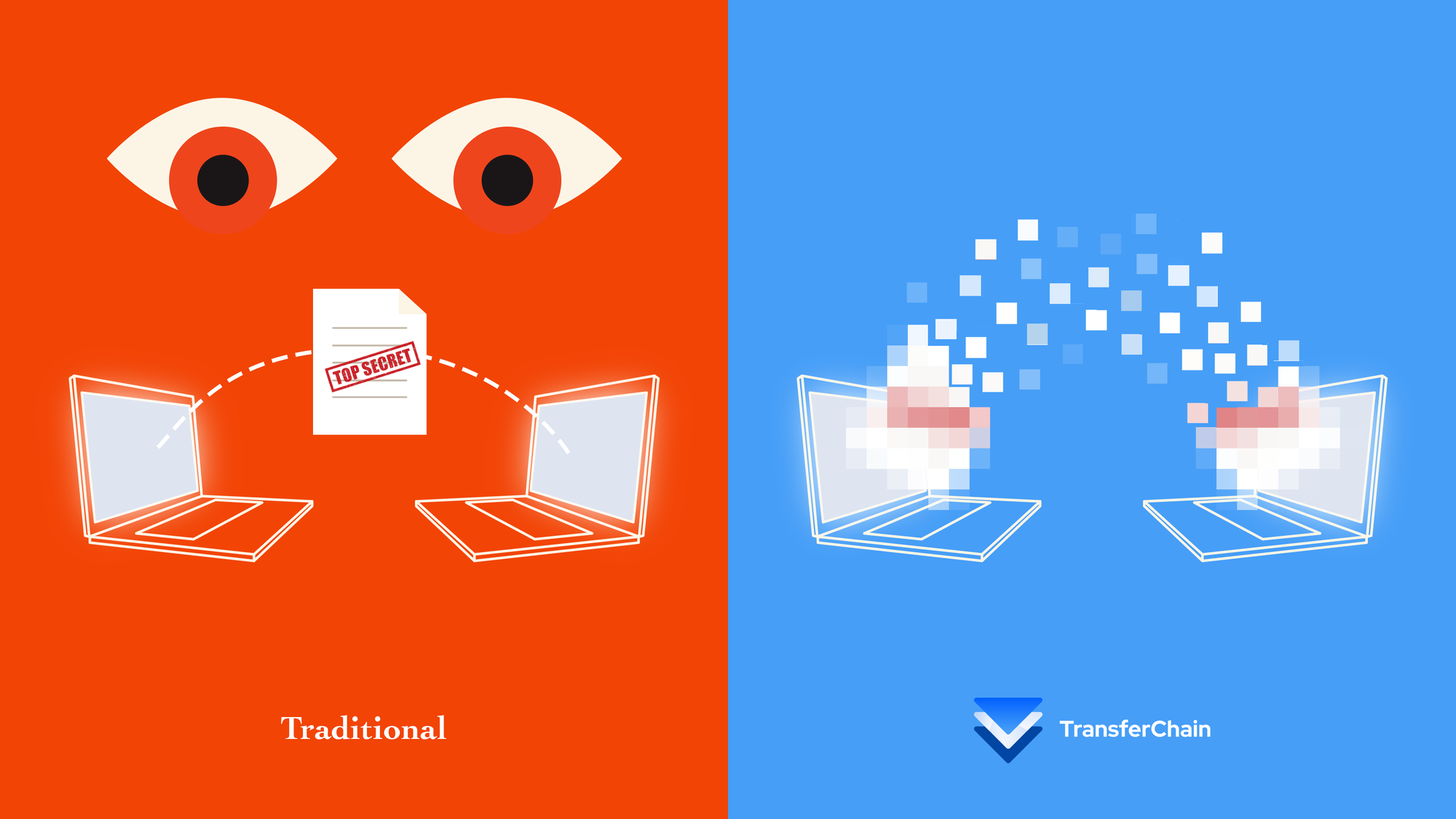
As TransferChain, we understand your need for secure, scalable, and modern solutions for Secure & Private cloud storage and file transfer.
Hence, we are offering a decentralized and distributed cloud system designed to meet the demands of today's digital landscape.
Why Choose TransferChain?
- Decentralized Architecture: TransferChain leverages a distributed cloud architecture to eliminate single points of failure, ensuring unmatched reliability and security.
- Advanced Security Protocols: With client side end-to-end encryption, zero-trust access models, and multi-factor authentication, TransferChain ensures your data is safe both in transit and at rest.
- Real-Time Monitoring: Gain instant insights into file transfer activities and proactively address potential risks with the Activity Log feature, which includes SIEM integration and is directly accessible via the Admin Panel.
- Built-In Compliance Support: TransferChain's decentralized and secure architecture inherently aligns with global data security standards, including but not limited to GDPR (Europe), TISAX, ISO 27001, and more, ensuring effortless compliance and maintenance.
Take Control of Your File Transfers Today
Don’t let outdated protocols hold your organization back. Upgrade to TransferChain and experience the power of secure, decentralized, and future-ready file transfers.
👉 Get Started with TransferChain Now
Or request a demo today to see how TransferChain can transform your data transfer workflows.
Frequently Asked Questions (FAQs)
Here are the frequently asked questions about SFTPs
What is the most Secure File Transfer Protocol?
The most secure file transfer protocol is one that ensures end-to-end encryption, protects data both in transit and at rest, and eliminates vulnerabilities associated with traditional methods. While SFTP provides encryption during transfer, it lacks built-in protection for stored data. TransferChain offers a fully encrypted, decentralized solution using Elliptic Curve Cryptography (secp256k1), AES-256, and zero-knowledge encryption, making it a superior choice for modern security needs.
What is the secure method of file transfer protocol?
A truly secure file transfer protocol should integrate strong encryption algorithms, secure key management, and robust authentication mechanisms. TransferChain achieves this through client-side key management, eliminating server-side key vulnerabilities and ensuring that encryption keys never leave the user’s device. Additionally, it employs forward secrecy and real-time monitoring, making it the most secure method for file transfers.
What Is the Difference Between FTPS and SFTP?
FTPS and SFTP both add security to file transfers, but they do so in different ways. FTPS uses SSL/TLS encryption for securing connections but does not inherently encrypt files. SFTP is based on SSH and encrypts both commands and data, providing a more secure transfer. However, both FTPS and SFTP lack modern security features like built-in automation, advanced access controls, and zero-knowledge encryption. TransferChain surpasses both by providing client-side end-to-end encryption, API-driven integrations, and a decentralized architecture that ensures complete data protection.


