
Beyond Encryption: How TransferChain Merges Security with User Experience
Ever struggled to find a balance between unparalleled security and an easy-to-use platform? Well, that's a thing of the past, gone are the days when robust security meant complex interfaces. TransferChain ends this dilemma. We combine truly secure and private cloud storage with a seamless user experience, making security feel like second nature, without all the hassle.
Our Approach
Our core belief is that a tech product's success goes beyond features to its design. Security products tend to be complex, presenting a significant barrier to widespread use. However, we know that even the most robust security systems are only as effective as their simplicity: The more straightforward and user-friendly the product is, the more consistently it will be used as intended.
TransferChain exemplifies this balance and redefines the standard for security products:
- It is built on cutting-edge security, including client-side end-to-end encryption, cryptographic file splitting, distributed cloud architecture, and blockchain authorization, all integrated with a user-friendly interface. Check our security page for more details about TransferChain’s security architecture.
- We cater to everyone, not just tech experts. By focusing on the synergy between top-tier security and intuitive design, we’re transforming security from a complex, niche tool into a practical, everyday resource for users of all levels.
To achieve that, our design process embodies both agility and practicality, skillfully navigating between the ideal design process and practical limitations. Every project at TransferChain has its unique path – launching new products or features involves in-depth market analysis and comprehensive user research, while updates or facelifts might rely more on informal customer feedback, design expertise, and internal insights. When we encounter risky assumptions during these updates or redesigns, we don't hesitate to conduct targeted testing, ensuring that our design decisions, no matter how significant or minor, always align with our core mission: to deliver secure, yet user-friendly solutions.
The Challenge: Making Secure Products User-Friendly
Integrating user-friendly design into cybersecurity is challenging. We've tackled this by understanding user needs and crafting features that meet these needs without compromising security.
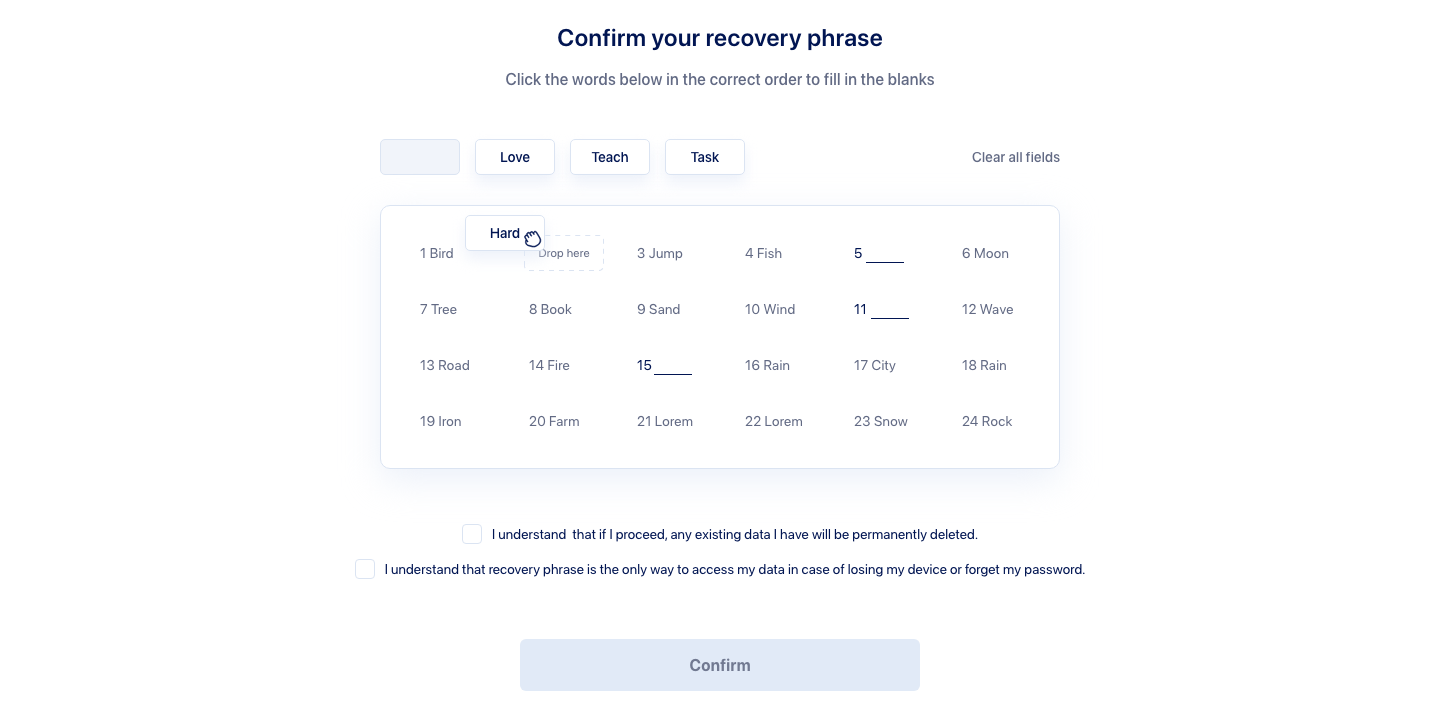
Streamlined Recovery Phrase Confirmation
Diverging from many platforms that depend on third-party services, TransferChain ensures that your keys are locally generated and stored on your device, encrypted with your password to guarantee your complete control and privacy. The confirmation process for the 24-word recovery phrase at TransferChain is designed with a dual purpose:
- To encourage users to securely store their recovery phrases.
- To confirm that they have effectively done so.
To achieve this, we employ a drag-and-drop and click-based method, tailored for speed and user convenience. The process is quick and intuitive using various cognitive styles, such as visual recognition or numerical sequencing. Also, it reduces the likelihood of errors commonly associated with manual input, and the ease of correcting misplaced words significantly reduces frustration.
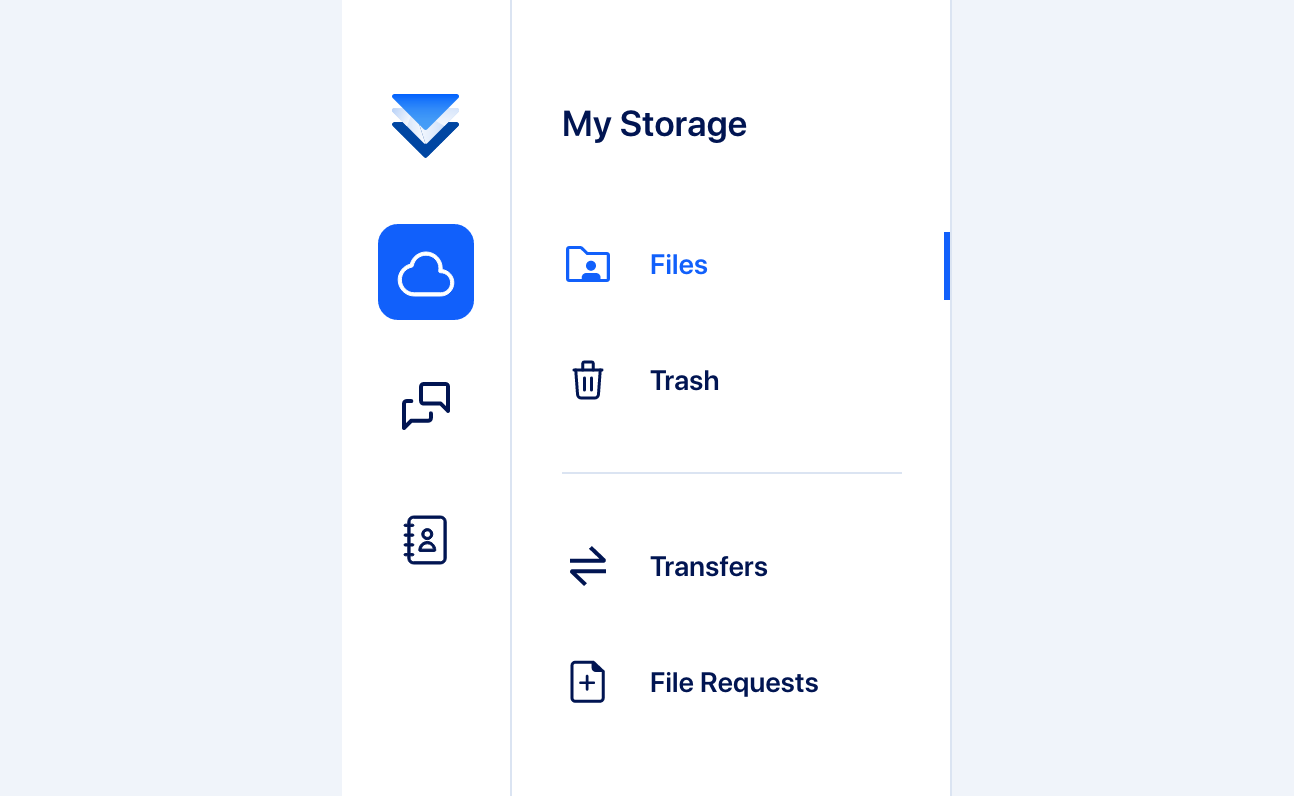
Intuitive Navigation and File Management
Our web app’s navigation is designed for ease of use, based on user insights gained from conducting card sorting tests. The outcome is a navigation system centered around content types for direct access to key functionalities, with secondary action-based navigation appearing contextually. This layered approach simplifies navigation by preventing an overload of options, creating an accessible and efficient user experience.
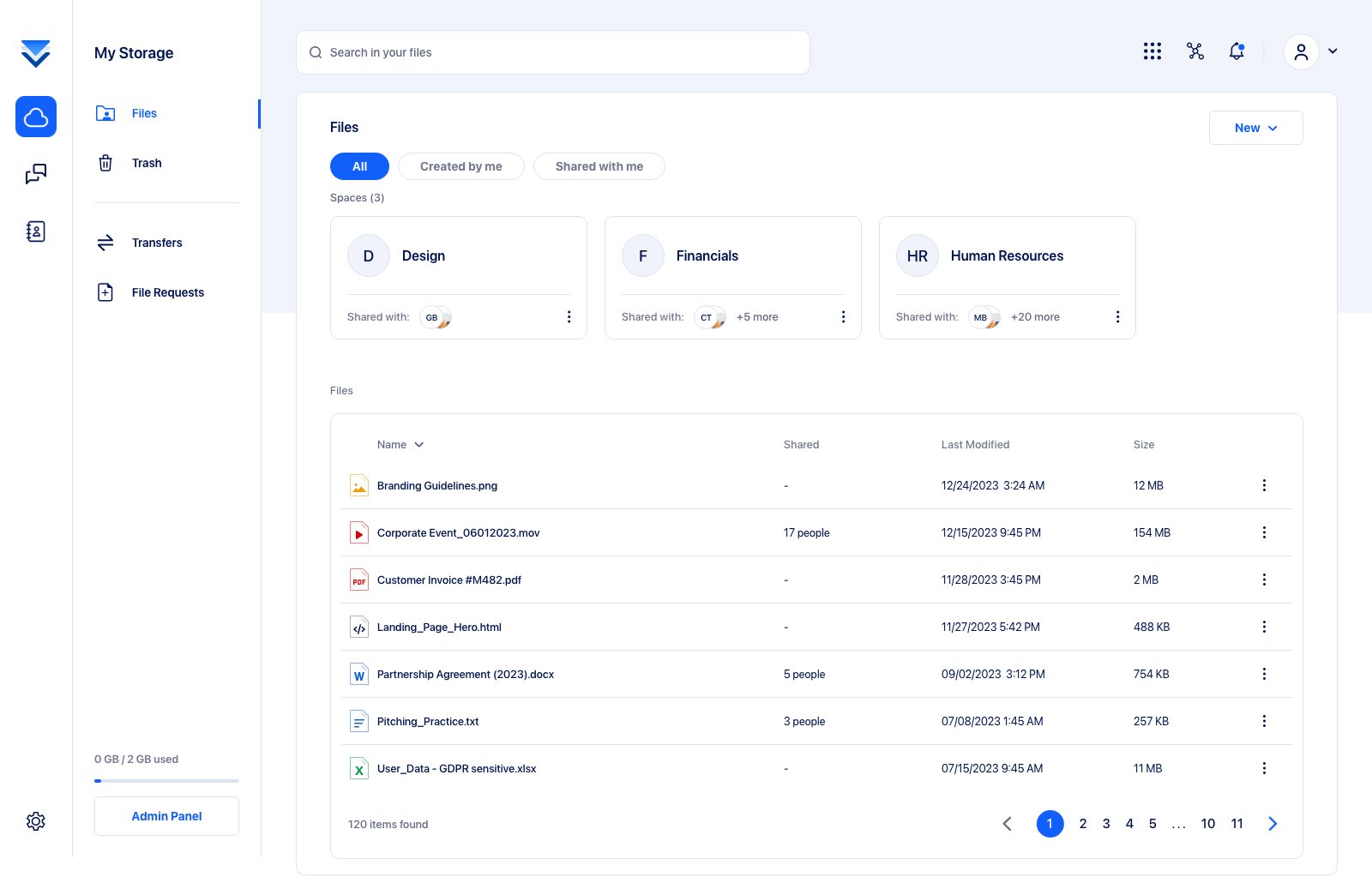
To simplify the content management we've employed clear and logical filter categories. By doing so, we’ve made it straightforward for users to locate and interact with content based on its source – whether they are personally created or uploaded, or those shared by others.
Transparent and Educative User Interactions
Understanding each action's implications in a secure digital environment is essential. For instance, our research has shown that users often hesitate to modify shared data due to a lack of understanding of how their actions might affect access rights and impact others. To address this, we’ve designed informative pop-ups around shared files to explicitly explain the consequences of actions like moving a shared file and fostering a sense of control and clarity. It eliminates the need for trial and error for users, ensuring that they are not left in the dark.
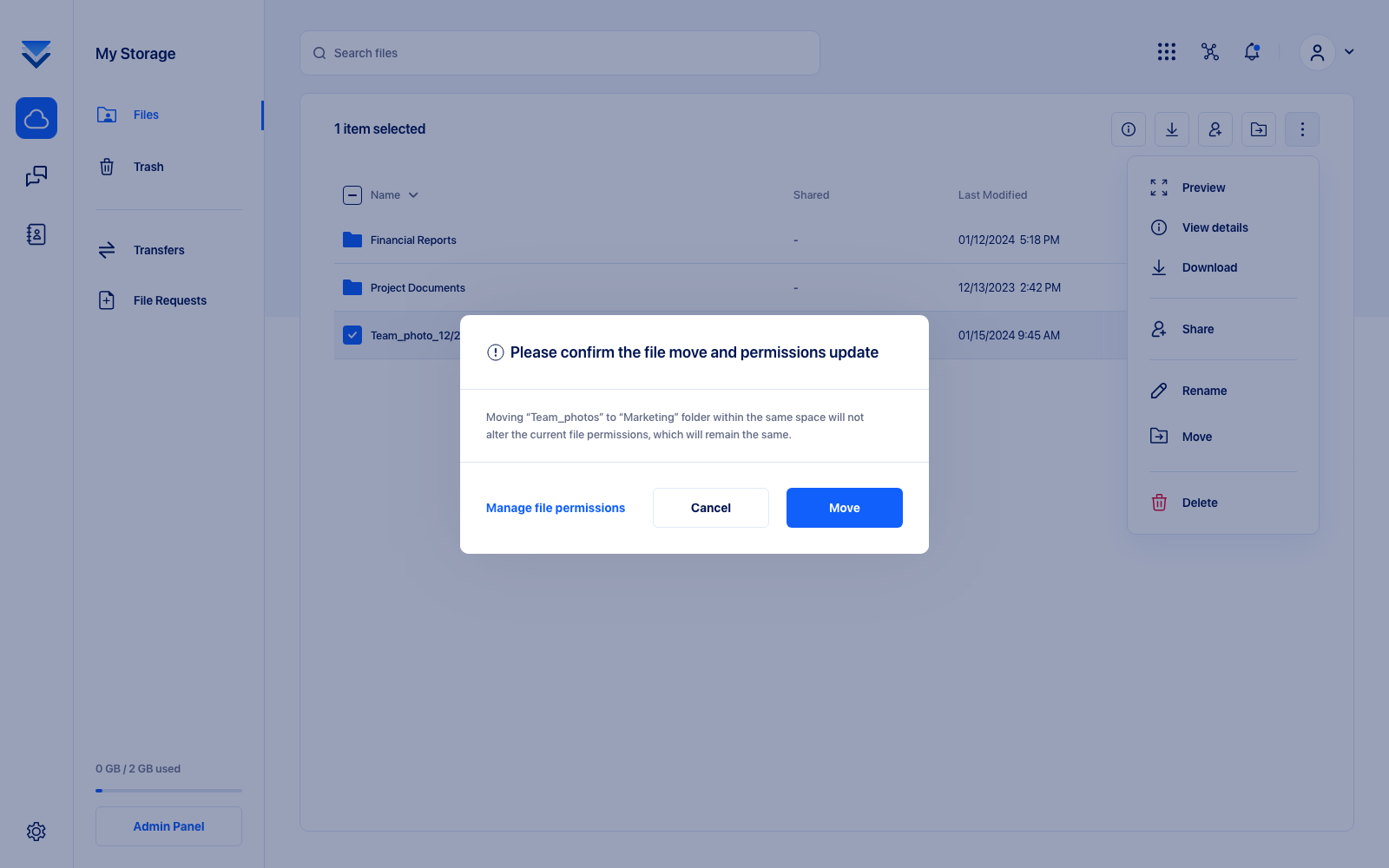
Building upon this foundation of transparency and education in user interactions, our design principles extend to other aspects of the platform as well. In the realm of file transfers, for instance, we've carefully curated the file transfer list to display active (non-expired) transfers by default. For those curious about their expired transfers, the interface transparently communicates that these files have been permanently deleted and are thus inaccessible. This intentional design choice not only helps in maintaining a clean and uncluttered user interface but also serves as an educational touchpoint. It reinforces our commitment to privacy and security by continuously reminding users about the secure and definitive deletion of their data.
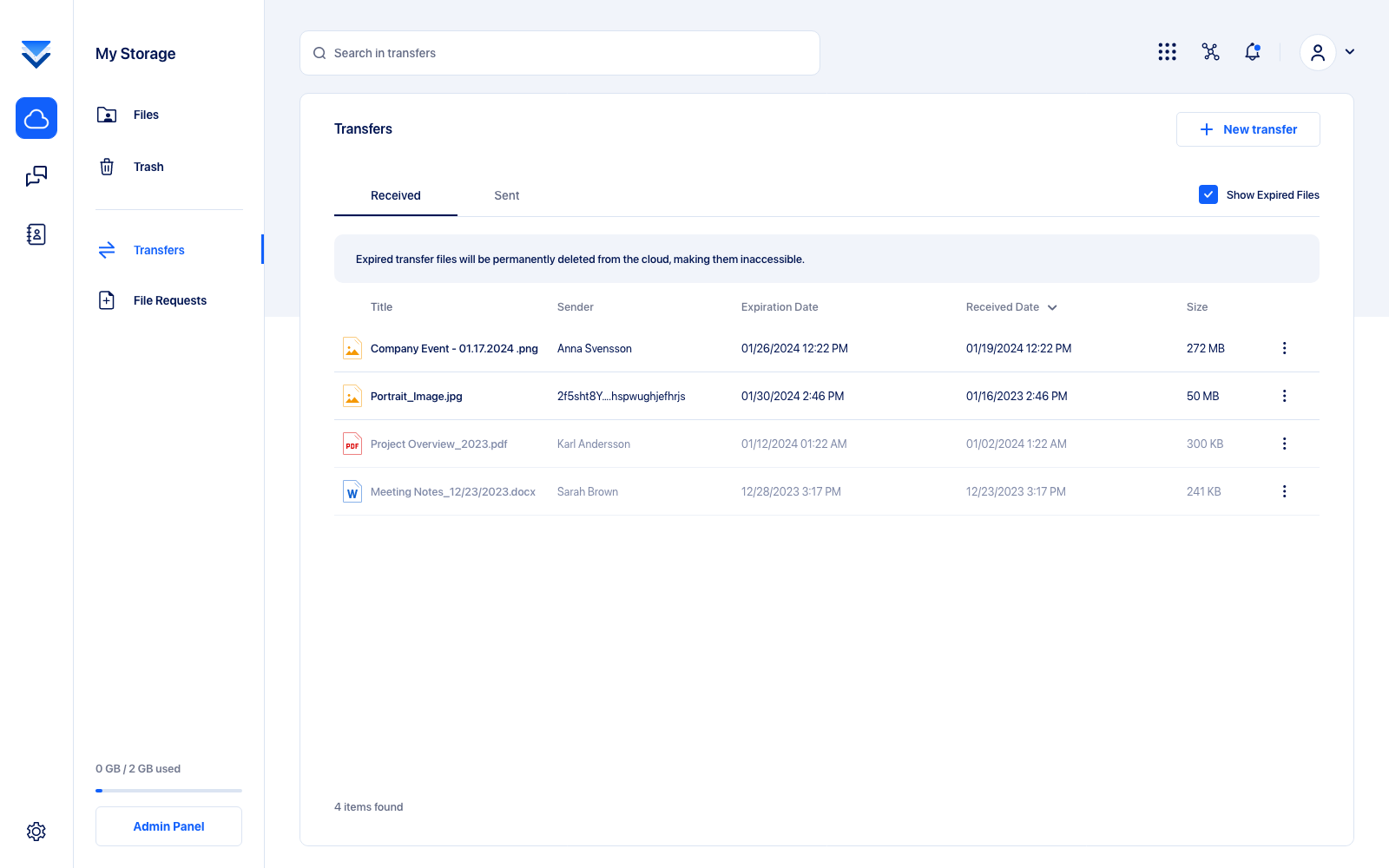
Advancing from our detailed exploration of user-friendly interfaces and advanced security features, TransferChain serves as a clear demonstration of the feasibility of blending sophisticated security with user accessibility. In each of these examples, we carefully balanced the need to convey security and privacy without overwhelming the user.
By bridging the gap between advanced security technology and everyday usability, TransferChain emerges as a pioneering force in the cybersecurity world, showcasing that security can be both highly effective and remarkably straightforward.
If you’re ready to start securing your privacy, you’re more than welcome to try TransferChain.
